The Intercept: Ecuador Cuts Internet Access for Julian Assange to Preserve Neutrality in U.S. Election »
Archive | October, 2016
For our Swedish followers…
5 July podcast – in Swedish.
No shit, Sherlock…
The investigatory powers tribunal, which is the only court that hears complaints against MI5, MI6 and GCHQ, said the security services operated secret regimes to collect vast amounts of personal communications data, tracking individual phone and web use and large datasets of confidential personal information, without adequate safeguards or supervision for more than 10 years.
The Guardian: UK security agencies unlawfully collected data for 17 years, court rules »
EU confusion about trade agreements and data protection
EDRi: Corporate-sponsored privacy confusion in the EU on trade and data protection »
EuroActiv: European Commission paralysed over data flows in TiSA trade deal »
Todays Assange frenzy
The day started with the rumor that Wikileaks editor in chief Julian Assange is dead. The reason seems to be the following mystifying tweets…
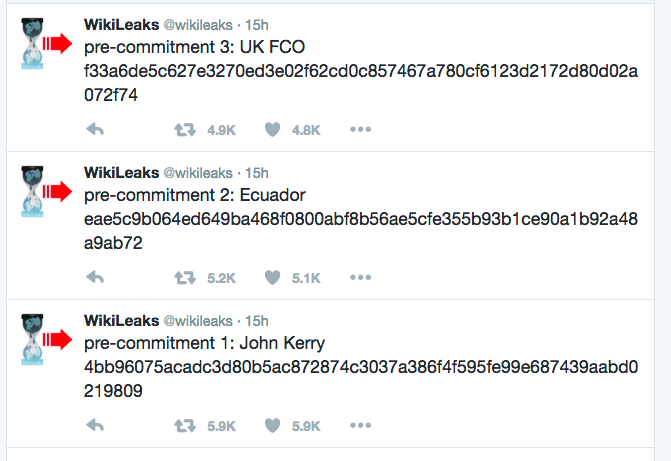
It’s possible that Assange made arrangements for a “dead man’s switch” release of content—that if he were arrested or otherwise rendered incommunicado, a cache of files held back would be released in an effort to damage the states and parties most likely involved in cutting him off from communication with WikiLeaks’ staff.
Wikileaks also tweeted that Assange’s Internet connection has been cut off by a “state party”. But nothing about Assange’s health.
At the same time, we learn that Swedish prosecutors will not be able to interview Assange this week. The date has been changed again – this time by Ecuador – to November 14. The reason is said to allow for Assange’s lawyers to attend.
If I may speculate, I guess that Assange would like to focus on the Clinton e-mails and the US election campaign before tackling the Swedish case. And there might be real security issues. Recently one of Assange’s UK lawyers was killed, falling in front of a London underground train. So maybe Assange simply doesn’t want any unknown people in his quarters before the US elections.
Meanwhile, in the US everyone is waiting for the next batch of leaked Clinton e-mails from Wikileaks.
/ HAX
Ars Technica: Assange’s Internet “intentionally severed by state party” »
Update, a tweet from Wikileaks: »We can confirm Ecuador cut off Assange’s internet access Saturday, 5pm GMT, shortly after publication of Clinton’s Goldman Sachs speechs.«
On TTIP, CETA, free trade and a free and open Internet
I’m a free marketeer. I believe that free trade would be hugely beneficial for all.
I also believe in a free and open Internet. Especially as it provides a level playing field on which entrepreneurs from all over the world can join a global market, 24/7.
And I’m not at all happy with politicians and bureaucrats trying to force me to choose between the two.
The CETA (EU-Canada) and TTIP (EU-US) trade agreements are problematic. CETA will undermine Europeans right to data protection and privacy online. The same goes for TTIP, which also might contain intellectual property regulations undermining the principle that Internet service providers are not responsible for what their customers are up to in their cables (the mere conduit principle). That would have huge implications, leading to a strictly controlled Internet where everything you are up to must be approved in advance. When it comes to TTIP, we still have no comprehensive information about what is going to be included or not when it comes to IP – as negotiations are carried out behind closed doors.
Also, the ISDS mechanism in these trade agreements will make a much needed and long overdue copyright reform impossible.
But then, again, these trade agreements are not really about free trade. They are about »harmonizing« rules and regulations. So, they are really about regulating trade.
If you want free trade, all you have to do is to get rid of customs fees and other trade barriers. That would benefit us and all of the humanity greatly. But that is not what the politic and bureaucratic elite hope for. They want to regulate and control. The EU even has a special sub-bureaucracy for »trade defense«.
So, I don’t buy into it when they claim that these »free trade agreements« are about free trade.
I’m standing with free trade. And I’m standing with a free and open Internet. It is perfectly possible and logical to combine these standpoints with being critical to CETA and TTIP.
/ HAX
CETA and your privacy
Thanks to the Snowden revelations, it was proven that Canada was conducting mass surveillance activities within the so-called “Five Eyes” arrangement. If brought to court, as the Austrian student Max Schrems did with the EU-US agreement on transfer of personal data (the “Safe Harbor agreement”), the adequacy status given by the EU could be overturned. However, if CETA is ratified, the EU would be prohibited from protecting personal data in this way.
EDRi: CETA puts the protection of our privacy and personal data at risk »
No memes please, we’re British
The UK’s public prosecutor has demanded that social media users who post “humiliating” photoshopped images and memes should face jail, as well as those who incite “virtual mobs” because they are “opposed to that person’s opinions”.
Breitbart: Trolls Who Post ‘Humiliating’ Memes Could Be Jailed under UK Guidelines »
Manning OK
After being missing for seven days, whistleblower Chelsea Manning has made contact. Her prison warders threw her into solitary for a week and didn’t tell her lawyers or friends where she was.
BoingBoing: Chelsea Manning has surfaced and is OK »
IoT: When toasters attack
While people have been discussing the possible threat of Artificial Intelligence (AI) – a totally different and very real threat has emerged: IT-attacks exploiting the Internet of things (IoT).
Simply put, a multitude of connected devices can be used in unexpected, unwanted and destructive ways. IT security expert Bruce Schneier explains in reference to a recent attack…
Instead of using traditional computers for their botnet, they used CCTV cameras, digital video recorders, home routers, and other embedded computers attached to the internet as part of the Internet of Things.
E.g. it can be about DDos-attacks or to set up a botnet to distribute malware.
Many devices used today are more or less unprotected. At Krebs on Security the victim of such an attack, Brian Krebs writes…
One of those default passwords — username: root and password: xc3511 — is in a broad array of white-labeled DVR and IP camera electronics boards made by a Chinese company called XiongMai Technologies. These components are sold downstream to vendors who then use it in their own products. (…)
“The issue with these particular devices is that a user cannot feasibly change this password,” said Flashpoint’s Zach Wikholm. “The password is hardcoded into the firmware, and the tools necessary to disable it are not present. Even worse, the web interface is not aware that these credentials even exist.”
This also raises the question of state-sponsored attacks. What if a country orders its electronics industry to include specific vulnerabilities, backdoors, malware etc. in its products?
For now, I guess awareness and an open discussion is the best protection. Also, there might be initiatives on a political level in the EU:
According to a report at Euractive.com, the Commission is planning the new IoT rules as part of a new plan to overhaul the European Union’s telecommunications laws. “The Commission would encourage companies to come up with a labeling system for internet-connected devices that are approved and secure,” wrote Catherine Stupp. “The EU labelling system that rates appliances based on how much energy they consume could be a template for the cybersecurity ratings.”
Links:
• We Need to Save the Internet from the Internet of Things »
• Who Makes the IoT Things Under Attack? »
• Europe to Push New Security Rules Amid IoT Mess »
• Commission plans cybersecurity rules for internet-connected machines »
/ HAX
